
The Benefits of IT Security – You Don’t Have to Be a Professional to Do It!
When it comes to keeping your data safe, there are a number of different ways that you can do it. So Today we will talk about The Benefits of IT […]

When it comes to keeping your data safe, there are a number of different ways that you can do it. So Today we will talk about The Benefits of IT […]

Hyper Automation brings together several components of process automation, integrating tools and technologies that amplify the ability to automate work. How to Use Hyper Automation in Your Business Hyper automation is […]

5 Fixes for Technology Security Issues You’re About to Face. Today, almost all digital content is accessible online. The number of people with access to the Internet has continued to […]

Securing Your Information Technology, Did you know that a security breach costs businesses and individuals every day? A security breach is the unauthorized access to data or other information, including […]

Mobile Device security is a growing concern for consumers and businesses that want to stay connected and stay safe. With so many new devices being released every month, it’s no […]

Phishing Attacks is the act of sending a fake email or message designed to trick users into falling for a scam. While it’s been around for a while, the prevalence […]

Web security and privacy is one of the biggest challenges facing online businesses today. And with the number of hackers constantly targeting smaller and medium-sized companies, it has never been […]
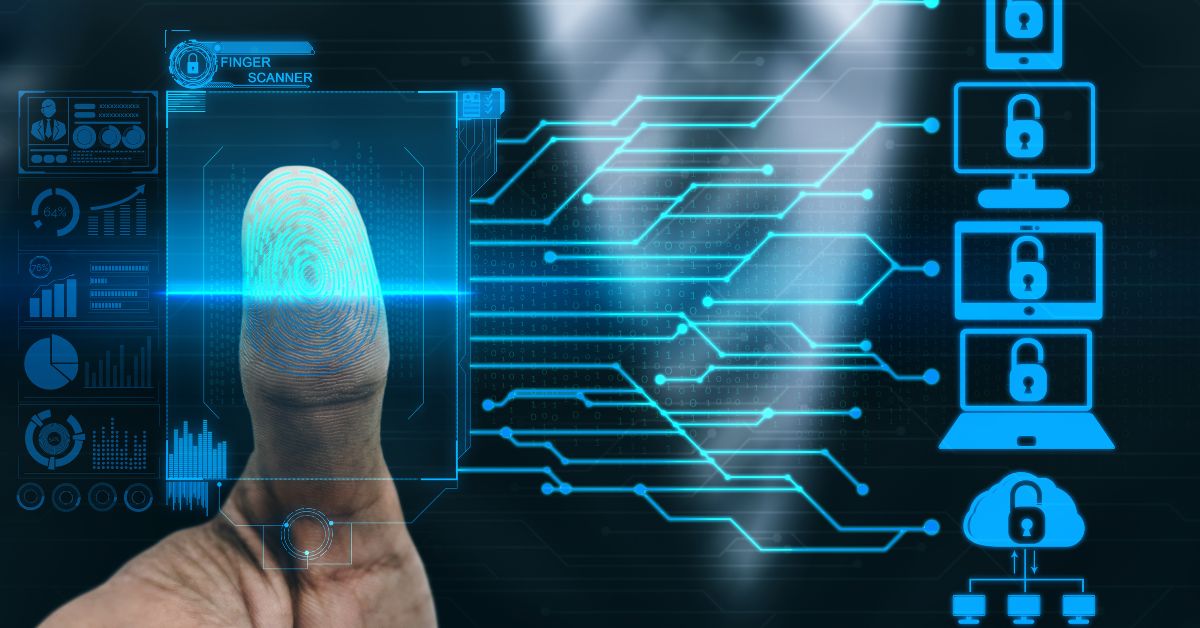
Biometric authentication is quickly becoming an essential security technology. It’s faster, more secure, and more reliable than passwords alone, yet it’s also much easier to use than fingerprint readers and […]

Biometrics is the science of using biological attributes to uniquely identify individuals, such as fingerprints or facial recognition. These natural attributes are used for identification because they are very reliable […]

When you think about it, the world is already a cyberphysical system. From computers and smartphones to thermostats and cars, cyber physical systems are becoming the new normal. These systems […]